The Code Book (24 page)

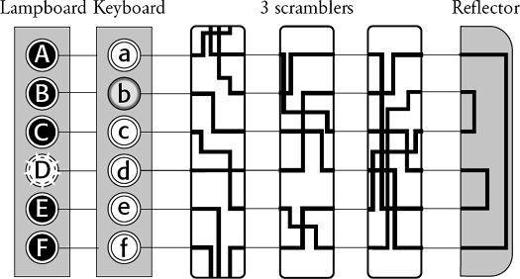
Figure 36
Scherbius’s design of the Enigma included a third scrambler and a reflector that sends the current back through the scramblers. In this particular setting, typing in b eventually illuminates D on the lampboard, shown here adjacent to the keyboard.
An operator wishes to send a secret message. Before encryption begins, the operator must first rotate the scramblers to a particular starting position. There are 17,576 possible arrangements, and therefore 17,576 possible starting positions. The initial setting of the scramblers will determine how the message is encrypted. We can think of the Enigma machine in terms of a general cipher system, and the initial settings are what determine the exact details of the encryption. In other words, the initial settings provide the key. The initial settings are usually dictated by a codebook, which lists the key for each day, and which is available to everybody within the communications network. Distributing the codebook requires time and effort, but because only one key per day is required, it could be arranged for a codebook containing 28 keys to be sent out just once every four weeks. By comparison, if an army were to use a onetime pad cipher, it would require a new key for every message, and key distribution would be a much greater task. Once the scramblers have been set according to the codebook’s daily requirement, the sender can begin encrypting. He types in the first letter of the message, sees which letter is illuminated on the lampboard, and notes it down as the first letter of the ciphertext. Then, the first scrambler having automatically stepped on by one place, the sender inputs the second letter of the message, and so on. Once he has generated the complete ciphertext, he hands it to a radio operator who transmits it to the intended receiver.
In order to decipher the message, the receiver needs to have another Enigma machine and a copy of the codebook that contains the initial scrambler settings for that day. He sets up the machine according to the book, types in the ciphertext letter by letter, and the lampboard indicates the plaintext. In other words, the sender typed in the plaintext to generate the ciphertext, and now the receiver types in the ciphertext to generate the plaintext—encipherment and decipherment are mirror processes. The ease of decipherment is a consequence of the reflector. From
Figure 36
we can see that if we type in b and follow the electrical path, we come back to D. Similarly, if we type in d and follow the path, then we come back to B. The machine encrypts a plaintext letter into a ciphertext letter, and, as long as the machine is in the same setting, it will decrypt the same ciphertext letter back into the same plaintext letter.
It is clear that the key, and the codebook that contains it, must never be allowed to fall into enemy hands. It is quite possible that the enemy might capture an Enigma machine, but without knowing the initial settings used for encryption, they cannot easily decrypt an intercepted message. Without the codebook, the enemy cryptanalyst must resort to checking all the possible keys, which means trying all the 17,576 possible initial scrambler settings. The desperate cryptanalyst would set up the captured Enigma machine with a particular scrambler arrangement, input a short piece of the ciphertext, and see if the output makes any sense. If not, he would change to a different scrambler arrangement and try again. If he can check one scrambler arrangement each minute and works night and day, it would take almost two weeks to check all the settings. This is a moderate level of security, but if the enemy set a dozen people on the task, then all the settings could be checked within a day. Scherbius therefore decided to improve the security of his invention by increasing the number of initial settings and thus the number of possible keys.
He could have increased security by adding more scramblers (each new scrambler increases the number of keys by a factor of 26), but this would have increased the size of the Enigma machine. Instead, he added two other features. First, he simply made the scramblers removable and interchangeable. So, for example, the first scrambler disk could be moved to the third position, and the third scrambler disk to the first position. The arrangement of the scramblers affects the encryption, so the exact arrangement is crucial to encipherment and decipherment. There are six different ways to arrange the three scramblers, so this feature increases the number of keys, or the number of possible initial settings, by a factor of six.
The second new feature was the insertion of a
plugboard
between the keyboard and the first scrambler. The plugboard allows the sender to insert cables which have the effect of swapping some of the letters before they enter the scrambler. For example, a cable could be used to connect the a and b sockets of the plugboard, so that when the cryptographer wants to encrypt the letter b, the electrical signal actually follows the path through the scramblers that previously would have been the path for the letter a, and vice versa. The Enigma operator had six cables, which meant that six pairs of letters could be swapped, leaving fourteen letters unplugged and unswapped. The letters swapped by the plugboard are part of the machine’s setting, and so must be specified in the codebook.
Figure 37
shows the layout of the machine with the plugboard in place. Because the diagram deals only with a six-letter alphabet, only one pair of letters, a and b, have been swapped.
There is one more feature of Scherbius’s design, known as the
ring
, which has not yet been mentioned. Although the ring does have some effect on encryption, it is the least significant part of the whole Enigma machine, and I have decided to ignore it for the purposes of this discussion. (Readers who would like to know about the exact role of the ring should refer to some of the books in the list of further reading, such as
Seizing the Enigma
by David Kahn. This list also includes two Web sites containing excellent Enigma emulators, which allow you to operate a virtual Enigma machine.)
Now that we know all the main elements of Scherbius’s Enigma machine, we can work out the number of keys, by combining the number of possible plugboard cablings with the number of possible scrambler arrangements and orientations. The following list shows each variable of the machine and the corresponding number of possibilities for each one:
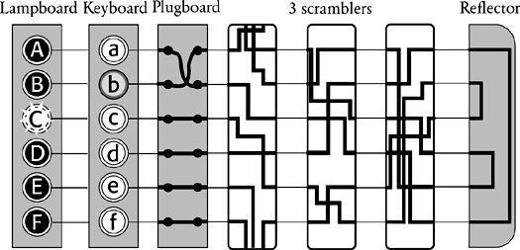
Figure 37
The plugboard sits between the keyboard and the first scrambler. By inserting cables it is possible to swap pairs of letters, so that, in this case, b is swapped with a. Now, b is encrypted by following the path previously associated with the encryption of a. In the real 26-letter Enigma, the user would have six cables for swapping six pairs of letters.
Scrambler orientations
. Each of the 3 scramblers can be set in one of 26 orientations. There are therefore
26 × 26 × 26 settings:
17,576
Scrambler arrangements
. The three scramblers (1, 2 and 3) can be positioned in any of the following six orders:
123, 132, 213, 231, 312, 321.
6
Plugboard
. The number of ways of connecting, thereby swapping, six pairs of letters out of 26 is enormous:
100,391,791,500
Total
. The total number of keys is the multiple of these three numbers: 17,576 × 6 × 100,391,791,500
≈10,000,000,000,000,000
As long as sender and receiver have agreed on the plugboard cablings, the order of the scramblers and their respective orientations, all of which specify the key, they can encrypt and decrypt messages easily. However, an enemy interceptor who does not know the key would have to check every single one of the 10,000,000,000,000,000 possible keys in order to crack the ciphertext. To put this into context, a persistent cryptanalyst who is capable of checking one setting every minute would need longer than the age of the universe to check every setting. (In fact, because I have ignored the effect of the rings in these calculations, the number of possible keys is even larger, and the time to break Enigma even longer.)
Since by far the largest contribution to the number of keys comes from the plugboard, you might wonder why Scherbius bothered with the scramblers. On its own, the plugboard would provide a trivial cipher, because it would do nothing more than act as a monoalphabetic substitution cipher, swapping around just 12 letters. The problem with the plugboard is that the swaps do not change once encryption begins, so on its own it would generate a ciphertext that could be broken by frequency analysis. The scramblers contribute a smaller number of keys, but their setup is continually changing, which means that the resulting ciphertext cannot be broken by frequency analysis. By combining the scramblers with the plugboard, Scherbius protected his machine against frequency analysis, and at the same time gave it an enormous number of possible keys.
Scherbius took out his first patent in 1918. His cipher machine was contained in a compact box measuring only 34 × 28 × 15 cm, but it weighed a hefty 12 kg.
Figure 39
shows an Enigma machine with the outer lid open, ready for use. It is possible to see the keyboard where the plaintext letters are typed in, and, above it, the lampboard which displays the resulting ciphertext letter. Below the keyboard is the plugboard; there are more than six pairs of letters swapped by the plugboard, because this particular Enigma machine is a slightly later modification of the original model, which is the version that has been described so far.
Figure 40
shows an Enigma with the cover plate removed to reveal more features, in particular the three scramblers.
Scherbius believed that Enigma was impregnable, and that its cryptographic strength would create a great demand for it. He tried to market the cipher machine to both the military and the business community, offering different versions to each. For example, he offered a basic version of Enigma to businesses, and a luxury diplomatic version with a printer rather than a lampboard to the Foreign Office. The price of an individual unit was as much as $30,000 in today’s prices.

Figure 38
Arthur Scherbius. (
photo credit 3.5
)
Unfortunately, the high cost of the machine discouraged potential buyers. Businesses said that they could not afford Enigma’s security, but Scherbius believed that they could not afford to be without it. He argued that a vital message intercepted by a business rival could cost a company a fortune, but few businessmen took any notice of him. The German military were equally unenthusiastic, because they were oblivious to the damage caused by their insecure ciphers during the Great War. For example, they had been led to believe that the Zimmermann telegram had been stolen by American spies in Mexico, and so they blamed that failure on Mexican security. They still did not realize that the telegram had in fact been intercepted and deciphered by the British, and that the Zimmermann debacle was actually a failure of German cryptography.