The Bletchley Park Codebreakers (42 page)
Read The Bletchley Park Codebreakers Online
Authors: Michael Smith

There were, of course, many transmissions in July 1941 that were not in depth. The research section had the chi-patterns and psi-patterns and they used a highly laborious method of setting the wheels and so deciphering the transmissions. It involved trying likely cribs as plain-text at the start to give putative key; then subtracting from the putative key the chi-pattern at all possible settings for each level; and hoping to recognize possible fragments of the extended psi-streams. It was a long time before their first success, but by April 1942 they had deciphered several transmissions.
Various features of Tunny that favoured the analyst were, from time to time, abandoned by the Germans. The first of these concerned the psi-patterns, and is best described in terms of an important symbol Δ. Δ before a symbol describing a stream of bits or characters means the stream formed by adding together each pair of consecutive bits or characters. So
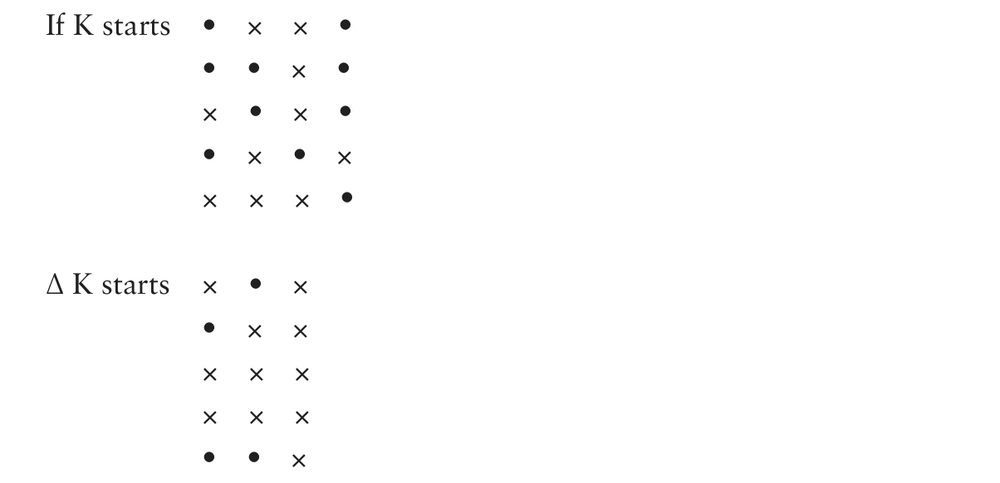
In all Tunny ever recovered, both the χ
i
and the Δχ
i
patterns for the i
th
level had as nearly as possible equal numbers of dots and crosses. Initially this was also true for the ψ
i
and the Δψ
i
patterns. It was this feature of the Δψ
i
patterns that had let Tutte in. In order for a particular
bit in Δψ
i
' to be a cross, both the total motor and Δψ
i
must be a cross. If
a
is the proportion of crosses in the total motor and
b
the proportion in Δψ
i
, then the proportion in Δψ
i
' is
a
b
. In early Tunny
b
was nearly ½, so that
ab
was much less than ½ and Δψ
i
' had considerably more dots than crosses. That meant that Δχ
i
was equal to ΔKi considerably more often than not, so that ΔK
i
written on a width appropriate for the i
th
level would be expected to give a majority of bits in each column that were equal to that bit in Δχ
i
. That was the feature that allowed Tutte to reconstruct Δχ
i
(and so χ
i
) for each level separately.
By the end of 1941, the German cryptographers plugged this gap. Thereafter the total motors and psi-patterns were always designed in such a way that
a b ≅ ½
.
After a drought, depths started to reappear in February 1942, and the research section read some of them and tried Tutte’s method without success. That was, of course, because by then
a b ≅ ½
and no attack in single streams could work.
They did eventually break the patterns for March and April 1942. In each month, there was a ‘near depth’, a pair of transmissions whose indicators differed only in the letters that gave the setting for two or three chi-wheels. They contrived a long and highly resourceful method of exploiting the differences of the χ-settings of those wheels, and eventually prised the whole thing open. They found that between March and April both the psi-patterns and the chi-patterns were different. Perhaps the psi-patterns changed quarterly, the chi-patterns monthly, and the μ-patterns daily.
The wheel settings were given by indicator letters, but they were not in letter order. When, however, two indicators had the same letter in a position, the wheel for that position started at the same place for the two transmissions. This meant that wheel-setting during a month gathered pace. The research section had such success setting wheels for March and April 1942 that it became clear that they needed a machine to do the decryption. The first was ordered and was delivered in June 1942.
For any month with no usable near-depth, a new method was needed to break the patterns. Another quite different (and equally laborious and resourceful) method was found. It exploited the twelve-letter
indicators, a special feature of what Tunny did at the first few letters of a transmission, and the routine starts to the plain-text. It was used to break the patterns of May, June and July 1942.
In July 1942 work on Tunny was handed over to a new section headed by Major Tester and named after him. It was formed from people already at Bletchley Park and they were supplemented by people from the Army and the ATS. The section inherited from the research section various methods but no royal road to success. Moreover, the two methods of wheel-breaking just mentioned were both defeated by German improvements. In August 1942 they began starting their transmission with ‘
Quatsch
’ (meaningless German words), so the method that depended on standard initial cribs was no use. In October 1942, the original experimental Tunny link was closed; in its place they started more and more links (on slightly modified machines) each with its own wheel-patterns. Thereafter, on all links, the clear twelve-letter indicator was replaced by a ‘QEP’ number; it referred to some list of settings available to the operators but not to Bletchley Park. Depths could be recognized from the repetition of the QEP number; but near-depths could not, even if there were any. So the method of wheel-breaking that used the letter-indicators was also denied to the Testery. Depths were still sent and read but there was at first no way of breaking wheel-patterns from the key-streams they provided.
In the summer of 1942, Alan Turing, already a legendary figure of Enigma cryptanalysis, attacked this problem of breaking patterns from key. He worked entirely on ΔK = Δχ + Δψ', exploiting a weakness of Δψ', namely that the chance that two bits of a character of Δψ' should be the same is
b
. (The two bits can only differ if, for that Δψ' character, there was a total motor cross so that there Δψ' = Δψ. The probability, therefore, that they differ is
a×2b
(1-
b
) = 1-
b when a b = ½
.)
The method started by making the assumption that, at some arbitrarily chosen point, there had been a total motor dot, so that
there Δψ' = / (the all dot character – a space in the teleprinter code). If that is right, at that place Δχ = ΔK and one Δχ bit is known at each level. These bits are cycled through the depth to give (by subtracting from ΔK) isolated bits of Δψ', ‘correct’ under the initial assumption. Since in a Δψ' character each pair of bits has a probability
b
of being equal, each such ‘correct’ Δψ' bit spawns putatively equal bits of Δψ' in the other four levels. Each such putative bit gives, by subtraction from ΔK, a putative Δχ bit that has a probability
b
of being right (under the initial assumption). These putative Δχ bits are then assembled onto a blank Δχ pattern for each of the five levels.
For instance, with a depth of 1,000 characters the original assumption places about twenty-four ‘correct’ Δχ
1
, bits, about thirty-two Δχ
2
bits, about thirty-four Δχ
3
bits and about thirty-eight Δχ
4
bits. Each spawns a single putative Δχ
5
bit, giving nearly 130 putative bits; so there will be five or six putative bits at each place on the twenty-three-long blank Δχ
5
pattern.
At this stage for all the levels the number of agreements and disagreements (between putative bits at the same place on a Δχ pattern) is counted. If the agreements do not exceed the disagreements convincingly the initial assumption is rejected, and another place is chosen to start the process and the whole thing is repeated.
Eventually the agreements do exceed the disagreements convincingly; fragmentary Δχ
i
patterns can be formed from the places where the putative Δχ
i
bits give a clear preference between dot and cross. These fragmentary patterns are then cycled through and subtracted from ΔK to give bits of Δψ'. At a place where Δψ' has three probable dots, it is assumed that there has been a motor dot and the remaining bits are taken to be dots, yielding two more Δχ bits. In this way the Δχ patterns are massaged against each other until complete correct Δχ patterns establish themselves. The rest is easy.
With this weapon known as Turingery, the Testery were in a position to break the patterns for each link/month that offered a substantial readable depth. The recovered patterns could be set against any other depth that could be read for twenty or more characters. There remained, however, the important problem of setting the bulk of the transmissions, that were not in depth.
In November 1942 Tutte proposed a way of setting known χ
1
and χ
2
patterns against a long enough stretch of cipher. He suggested comparing Δχ
1
+ Δχ
2
with ΔZ
1
+ ΔZ
2
. The idea is that (ΔZ
1
+ ΔZ
2
) – (Δχ
1
+ Δχ
2
) = (ΔP
1
+ ΔP
2
) + (Δψ
1
' + Δψ
2
'). For each character the probability that (Δψ
1
' + Δψ
2
') is a dot is
b
(when, as now,
ab
= 1/2). The value of
b
tended to be about 0.7. Results from statistics of plain-text had shown that (ΔP
1
+ ΔP
2
) is also considerably more likely to be dot than cross. Consequently (Δχ
1
+ Δχ
2
) is expected to be equal to (ΔZ
1
+ ΔZ
2
) noticeably more often than not.
Tutte devised a way of testing all the possible pairs of settings for χ
1
and χ
2
against a transmission of about 4,000 characters, and found a significantly good answer. The other chi-wheels were then set using similar methods and the psi-wheels and motor wheels followed. This was a striking achievement, but too slow to open an avenue to the goal of setting known patterns in useful quantities. It did, however, in March 1943, play an important part in diagnosing a new motor limitation.
In February 1943, the new Tunny machines had new features. These were ‘limitations’ that influenced the extension of the psi-stream. The basic motor was as before, but the psi-stream was only extended when the basic motor stream was at a dot and also the limitation stream was a cross. On a link known to Bletchley Park as Codfish, when chi-and psi-patterns had been set, the extensions of the psi-stream only partly agreed with any possible μ'
37
. The Testery analysed the divergences and found that they only came when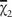 (the bit of χ
(the bit of χ
2
one place back) was a dot; the psi-stream was extended only when μ'
37
was a dot and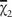 was a cross.
was a cross.
In March 1943, the link known as Herring introduced as the limitation stream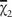 +
+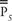 , the sum of χ
, the sum of χ
2
one back and P
5
two back. When in a system the key depends on previous plain-text, it is said to be ‘autoclave’, self-keying. This has two effects, one serious for us. Two transmissions with the same QEP numbers would have the same
starting positions for their wheels, but, having different P
5
bits, they would eventually have different extensions to their psi-wheels and so have different keys. Apparent depths would soon cease to be in depth and could no longer be read. The second feature was unfortunate for the Germans. Poor radio reception would often cause the receiver to get a false Z
5
bit and so a false P
5
bit, which could throw the decipherment out from then on. They had so much trouble with this autoclave feature that it was soon abandoned and only resumed in December 1943.