The Code Book (7 page)

By the fourteenth century the use of cryptography had become increasingly widespread, with alchemists and scientists using it to keep their discoveries secret. Although better known for his literary achievements, Geoffrey Chaucer was also an astronomer and a cryptographer, and he is responsible for one of the most famous examples of early European encryption. In his
Treatise on the Astrolabe
he provided some additional notes entitled “The Equatorie of the Planetis,” which included several encrypted paragraphs. Chaucer’s encryption replaced plaintext letters with symbols, for example b with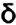 . A ciphertext consisting of strange symbols rather than letters may at first sight seem more complicated, but it is essentially equivalent to the traditional letter-for-letter substitution. The process of encryption and the level of security are exactly the same.
. A ciphertext consisting of strange symbols rather than letters may at first sight seem more complicated, but it is essentially equivalent to the traditional letter-for-letter substitution. The process of encryption and the level of security are exactly the same.
By the fifteenth century, European cryptography was a burgeoning industry. The revival in the arts, sciences and scholarship during the Renaissance nurtured the capacity for cryptography, while an explosion in political machinations offered ample motivation for secret communication. Italy, in particular, provided the ideal environment for cryptography. As well as being at the heart of the Renaissance, it consisted of independent city states, each trying to outmaneuver the others. Diplomacy flourished, and each state would send ambassadors to the courts of the others. Each ambassador received messages from his respective head of state, describing details of the foreign policy he was to implement. In response, each ambassador would send back any information that he had gleaned. Clearly there was a great incentive to encrypt communications in both directions, so each state established a cipher office, and each ambassador had a cipher secretary.
At the same time that cryptography was becoming a routine diplomatic tool, the science of cryptanalysis was beginning to emerge in the West. Diplomats had only just familiarized themselves with the skills required to establish secure communications, and already there were individuals attempting to destroy this security. It is quite probable that cryptanalysis was independently discovered in Europe, but there is also the possibility that it was introduced from the Arab world. Islamic discoveries in science and mathematics strongly influenced the rebirth of science in Europe, and cryptanalysis might have been among the imported knowledge.
Arguably the first great European cryptanalyst was Giovanni Soro, appointed as Venetian cipher secretary in 1506. Soro’s reputation was known throughout Italy, and friendly states would send intercepted messages to Venice for cryptanalysis. Even the Vatican, probably the second most active center of cryptanalysis, would send Soro seemingly impenetrable messages that had fallen into its hands. In 1526, Pope Clement VII sent him two encrypted messages, and both were returned having been successfully cryptanalyzed. And when one of the Pope’s own encrypted messages was captured by the Florentines, the Pope sent a copy to Soro in the hope that he would be reassured that it was unbreakable. Soro claimed that he could not break the Pope’s cipher, implying that the Florentines would also be unable to decipher it. However, this may have been a ploy to lull the Vatican cryptographers into a false sense of security-Soro might have been reluctant to point out the weaknesses of the Papal cipher, because this would only have encouraged the Vatican to switch to a more secure cipher, one that Soro might not have been able to break.
Elsewhere in Europe, other courts were also beginning to employ skilled cryptanalysts, such as Philibert Babou, cryptanalyst to King Francis I of France. Babou gained a reputation for being incredibly persistent, working day and night and persevering for weeks on end in order to crack an intercepted message. Unfortunately for Babou, this gave the king ample opportunity to carry on a long-term affair with his wife. Toward the end of the sixteenth century the French consolidated their codebreaking prowess with the arrival of François Viète, who took particular pleasure in cracking Spanish ciphers. Spain’s cryptographers, who appear to have been naive compared with their rivals elsewhere in Europe, could not believe it when they discovered that their messages were transparent to the French. King Philip II of Spain went as far as petitioning the Vatican, claiming that the only explanation for Viète’s cryptanalysis was that he was an “archfiend in league with the devil.” Philip argued that Viète should be tried before a Cardinal’s Court for his demonic deeds; but the Pope, who was aware that his own cryptanalysts had been reading Spanish ciphers for years, rejected the Spanish petition. News of the petition soon reached cipher experts in various countries, and Spanish cryptographers became the laughingstock of Europe.
The Spanish embarrassment was symptomatic of the state of the battle between cryptographers and cryptanalysts. This was a period of transition, with cryptographers still relying on the monoalphabetic substitution cipher, while cryptanalysts were beginning to use frequency analysis to break it. Those yet to discover the power of frequency analysis continued to trust monoalphabetic substitution, ignorant of the extent to which cryptanalysts such as Soro, Babou and Viète were able to read their messages.
Meanwhile, countries that were alert to the weakness of the straightforward monoalphabetic substitution cipher were anxious to develop a better cipher, something that would protect their own nation’s messages from being unscrambled by enemy cryptanalysts. One of the simplest improvements to the security of the monoalphabetic substitution cipher was the introduction of
nulls
, symbols or letters that were not substitutes for actual letters, merely blanks that represented nothing. For example, one could substitute each plain letter with a number between 1 and 99, which would leave 73 numbers that represent nothing, and these could be randomly sprinkled throughout the ciphertext with varying frequencies. The nulls would pose no problem to the intended recipient, who would know that they were to be ignored. However, the nulls would baffle an enemy interceptor because they would confuse an attack by frequency analysis. An equally simple development was that cryptographers would sometimes deliberately misspell words before encrypting the message. Thys haz thi ifekkt off diztaughting thi ballans off frikwenseas—making it harder for the cryptanalyst to apply frequency analysis. However, the intended recipient, who knows the key, can unscramble the message and then deal with the bad, but not unintelligible, spelling.
Another attempt to shore up the monoalphabetic substitution cipher involved the introduction of codewords. The term
code
has a very broad meaning in everyday language, and it is often used to describe any method for communicating in secret. However, as mentioned in the Introduction, it actually has a very specific meaning, and applies only to a certain form of substitution. So far we have concentrated on the idea of a substitution cipher, whereby each letter is replaced by a different letter, number or symbol. However, it is also possible to have substitution at a much higher level, whereby each word is represented by another word or symbol—this would be a code. For example,

Technically, a
code
is defined as substitution at the level of words or phrases, whereas a
cipher
is defined as substitution at the level of letters. Hence the term
encipher
means to scramble a message using a cipher, while
encode
means to scramble a message using a code. Similarly, the term
decipher
applies to unscrambling an enciphered message, and
decode
to unscrambling an encoded message. The terms
encrypt
and
decrypt
are more general, and cover scrambling and unscrambling with respect to both codes and ciphers.
Figure 7
presents a brief summary of these definitions. In general, I shall keep to these definitions, but when the sense is clear, I might use a term such as “codebreaking” to describe a process that is really “cipher breaking”-the latter phrase might be technically accurate, but the former phrase is widely accepted.

Figure 7
The science of secret writing and its main branches.
At first sight, codes seem to offer more security than ciphers, because words are much less vulnerable to frequency analysis than letters. To decipher a monoalphabetic cipher you need only identify the true value of each of the 26 characters, whereas to decipher a code you need to identify the true value of hundreds or even thousands of codewords. However, if we examine codes in more detail, we see that they suffer from two major practical failings when compared with ciphers. First, once the sender and receiver have agreed upon the 26 letters in the cipher alphabet (the key), they can encipher any message, but to achieve the same level of flexibility using a code they would need to go through the painstaking task of defining a codeword for every one of the thousands of possible plaintext words. The codebook would consist of hundreds of pages, and would look something like a dictionary. In other words, compiling a codebook is a major task, and carrying it around is a major inconvenience.
Second, the consequences of having a codebook captured by the enemy are devastating. Immediately, all the encoded communications would become transparent to the enemy. The senders and receivers would have to go through the painstaking process of having to compile an entirely new codebook, and then this hefty new tome would have to be distributed to everyone in the communications network, which might mean securely transporting it to every ambassador in every state. In comparison, if the enemy succeeds in capturing a cipher key, then it is relatively easy to compile a new cipher alphabet of 26 letters, which can be memorized and easily distributed.
Even in the sixteenth century, cryptographers appreciated the inherent weaknesses of codes, and instead relied largely on ciphers, or sometimes
nomenclators
. A nomenclator is a system of encryption that relies on a cipher alphabet, which is used to encrypt the majority of a message, and a limited list of codewords. For example, a nomenclator book might consist of a front page containing the cipher alphabet, and then a second page containing a list of codewords. Despite the addition of codewords, a nomenclator is not much more secure than a straightforward cipher, because the bulk of a message can be deciphered using frequency analysis, and the remaining encoded words can be guessed from the context.
As well as coping with the introduction of the nomenclator, the best cryptanalysts were also capable of dealing with badly spelled messages and the presence of nulls. In short, they were able to break the majority of encrypted messages. Their skills provided a steady flow of uncovered secrets, which influenced the decisions of their masters and mistresses, thereby affecting Europe’s history at critical moments.
Nowhere is the impact of cryptanalysis more dramatically illustrated than in the case of Mary Queen of Scots. The outcome of her trial depended wholly on the battle between her codemakers and Queen Elizabeth’s codebreakers. Mary was one of the most significant figures of the sixteenth century-Queen of Scotland, Queen of France, pretender to the English throne-yet her fate would be decided by a slip of paper, the message it bore, and whether or not that message could be deciphered.